Initial Analysis
We start with an .img file, which represents the contents of a USB drive. The first step is to check if there’s any recognizable partition information.
Checking the Image File
First, let’s inspect the file using fdisk:
fdisk -l usb.img
Disk usb.img: 256 MiB, 268435456 bytes, 524288 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xf4fa0c7e
The output shows that there are no partitions, which makes sense since the challenge involves a deleted partition. However, this doesn’t mean the data is gone, it just means the system doesn’t know where the partition starts.
Recovering the Partition Table
Since the partition was deleted but not overwritten, we can use testdisk, a tool designed for recovering lost partitions.
testdisk usb.img
- Select
wedding_usb.imgand choose[Proceed]. - Choose [Intel] if prompted for a partition table type.
- Select [Analyse] and then [Quick Search] to scan for lost partitions.
- Since
testdiskdetects the deleted partition, select it and choose [Write] to restore it.
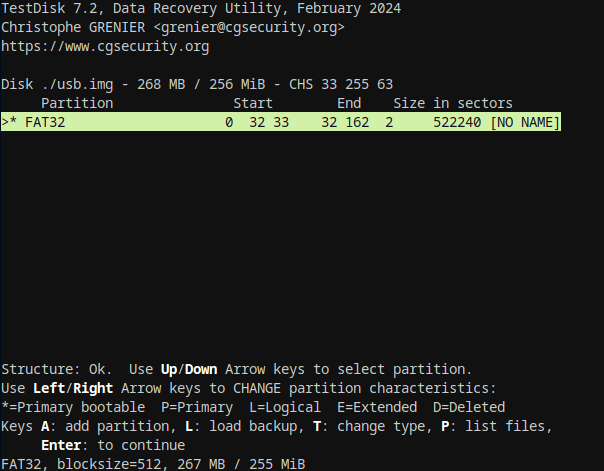
The output shows that testdisk successfully found the deleted partition and we were able to restored it. Now, we can proceed to mount the image and explore the recovered data.
Mounting the Recovered Partition
With the partition table restored, we can mount the image to access the files. First, we check the partition layout:
sudo kpartx -av usb.img
add map loop0p1 (254:3): 0 522240 linear 7:2 2048
This maps the partitions inside the .img file as loop devices (e.g., /dev/mapper/loop0p1).
Now, we mount the recovered partition:
sudo mkdir /mnt/recovered && mount /dev/mapper/loop0p1 /mnt/recovered
If we look at the files, nothing immediately looks to have a flag, so there’s one last trick to this challenge.
There’s a hidden folder in the root of the partition named .Meta, looking in that folder, we see a folder structure, that at it’s end becomes /.Meta/CTF/{n/0/t/_/ev/3n/_/d3/l3t/10n/_/c4/n/_/s3/part/3_/u/5}. Removing the slashes from the path gives us the flag!
MetaCTF{n0t_ev3n_d3l3t10n_c4n_s3part3_u5}