
Image credit: u/Hunor_Deak on Reddit
In this thinly veiled excuse to share my current hyperfixation CTF challenge, you are tasked to make sense of a seemingly incomprehensible mess of data that supposedly comes from an elusive cyber actor obsessed with vintage technology. Let’s walk through the process of solving this challenge:
The Basics
As with any new challenge of unknown files, let’s get the super-simple-stuff out of the way first, starting with file:
Well, it was worth a shot. Next, let’s just take a look to see what sort of “incomprehensible data” we’re looking at:
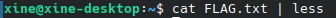
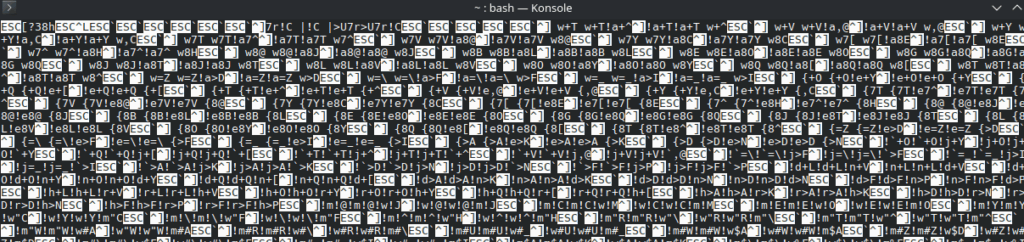
Yup, that is indeed incomprehensible. But, oddly, it’s incomprehensible in a very uniform way. Herein lies our first hint. Notice that by piping the output of cat into less, it gives us human-readable replacements for non-displayable ASCII characters, such as 0x1b (ESC, ANSI escape character) and 0x1D (^], “group separator”). Get it yet? What we’re looking at is a complicated series of ASCII escape sequences, the same type that would be used to make an old-school serial terminal do some seriously cool things.
Digging deeper
Let’s take a closer look at the beginning of the file:
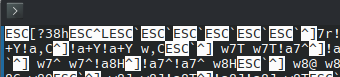
Notice that the first section of the file has the string ESC[?38h? ANSI escape sequences allow you to change the “screen mode” of the terminal with standardized modes such as ESC[=13h (320 x 200 color graphics) or ESC[=3h (80 x 25 color text), if you terminal supports it. To get some terminology out of the way, the opening bracket ([) in an ANSI control sequence is called a Control Sequence Inducer (CSI). Now, with a little research (check out this github page for more info), it seems that the combination of ESC + CSI + ? usually means that the code is attempting to tell the terminal to enter a certain private screen mode (a mode not defined in the ANSI spec, usually only supported by a specific model or manufacturer). So now we need to figure out what “screen mode” our file is attempting to enter.
Helpfully, the user who made the above Github guide links us to the reference for XTerm control sequences. Since our bad guy is probably not literally hacking on tech from the 80s, it’s a safe bet to say that he’s probably using a terminal emulator and not a real dumb terminal, so this is a good start. Let’s see if we can find out mysterious “38h” screen mode…
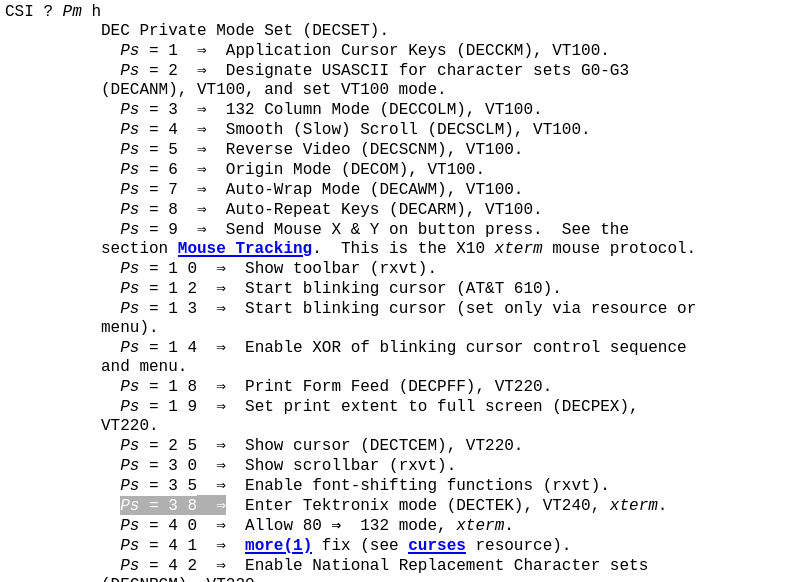
Well would you look at that. Not only have we figured out that our mystery data is trying to put us in “Tektronix” mode, we can also see by the xterm at the end of this line that this command is specifically used for xterm and not for any other terminal.
A quick history lesson
You may be asking yourself what’s so special about Tektronix mode – what’s so special about this esoteric, 1980s-era tech? Well, I’m going to assume that you understand how a normal screen works; you have a grid of pixels on your screen, and the computer chooses to “flash” individual pixels each clock cycle. Flash the pixels fast enough, and you have what appears to our human eyes as a solid display. The division of images into individual pixels is often called “raster graphics”.
The problem with raster graphics in the world of dumb terminals is one of memory: in a world in which you used “dumb” terminals to connect to a mainframe computer, RAM came at a premium. To store a frame-buffer of each individual pixel of the screen would have been prohibitively expensive for any dumb terminal to do. So, Tektronix came up with a different solution: continuous illumination vector graphics.
To put it very simply, a Tektronix terminal display works kind of like a CRT Etch-A-Sketch; the terminal recieves two sets of coordinates and uses one electron gun to draw a line, while another electron gun constantly keeps lighting up the whole screen. Due to the science behind CRT displays, the line drawn by the first electron gun will stay there, perfectly illuminated, until the terminal is instructed to clear the screen. No memory needed, and the vector graphics method gave developers the ability to display some seriously high-quality graphics for the time. The tradeoff, of course, is that other terminals would be completely unable to parse information meant for a Tektronix terminal’s graphics mode, since they were reliant on raster “pixel” information.
Reading the message
If you made it through the history lesson, good on you. If you skipped it, that’s understandable but still, shame on you. Now, let’s read this file.
If you’re one of the six people left who still daily-drive xterm as your primary terminal emulator, hats off to you, you can just skip ahead to the end. For the rest of us, we’re going to need to install xterm on our Linux distribution of choice. As discussed earlier, xterm has built-in support for Tektronix-style terminal emulation, and will in fact immediately open a Tektronix emulation window whenever it encounters the aforementioned escape sequence ESC[?38h. What does that mean for us?
Well, it means that the solution to this challenge is quite literally as simple as running cat from xterm:
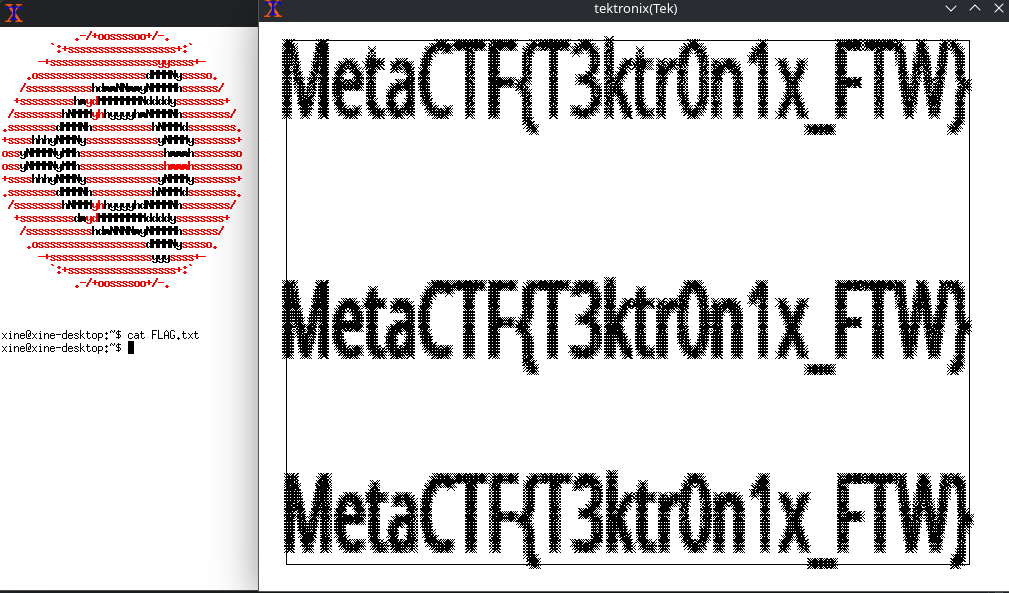
And there you have it: our mystery data was, after all, just a series of graphics commands for the Tektronix 4010-series terminal to display an image with our flag. I hope you all enjoyed the throwback to classic tech, and maybe learned something about ANSI escape sequences along the way!