PRODUCTS
Competition-Based Training
Upskill and engage your team with hands-on gamified training.
Jeopardy-Style CTF Competitions
Custom competition-based training for teams at a variety of difficulty and skill levels.
Attack & Defense CTF Competitions
JEOPARDY-STYLE CTF COMPETITIONS
Features for Managers/Administrators:
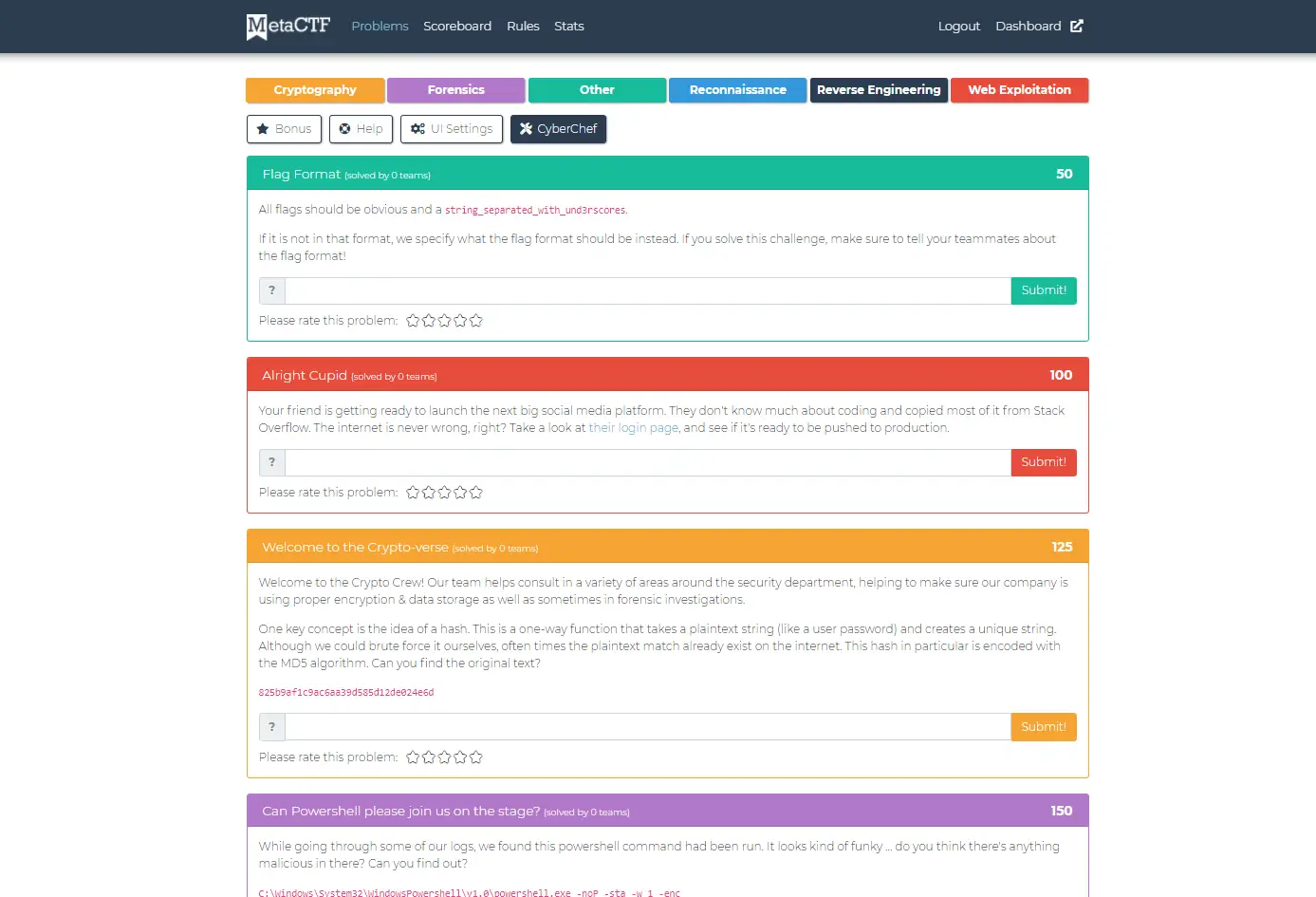
Flexible Setup Options
Tailor competitions to your preferences, choosing between individual or team-based formats.
Customizable Dashboards
Craft competition dashboards with essential information, including rules, timer, FAQs, prizes, and more.
Scoreboard Control
Display or hide scoreboards, intensifying competition suspense until the end.
Scheduled Challenge Releases
Increase engagement by scheduling when challenges are released.
Virtual Machines with Tools
Provide participants with downloadable security tools within virtual machines, avoiding local machine installations.
Features for Competition Participants:
Inclusive for All Levels
Suitable for participants at varying skill levels.
Point System
Earn points based on challenge difficulty, with options for dynamic points influenced by other teams’ progress.
Customizable Scoreboards
Break down scoreboards by skill level, functional group, department, geography, or other determinants.
Cascading Hint System
Navigate challenges seamlessly with a cascading hint system, unlocking hints for free or at a point cost.
Built-In CTF Tools
Utilize integrated tools like Cyber Chef for a seamless experience.
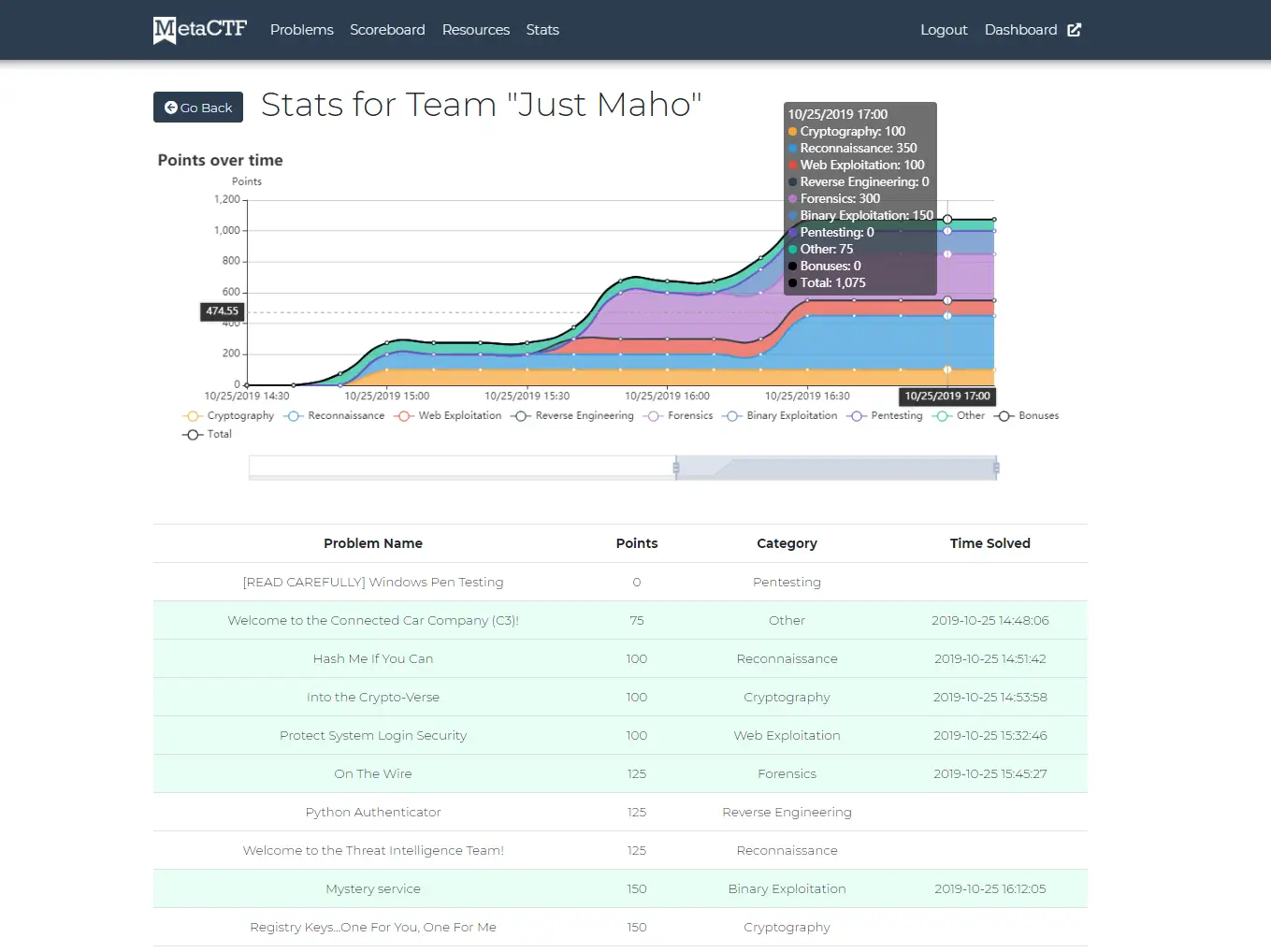
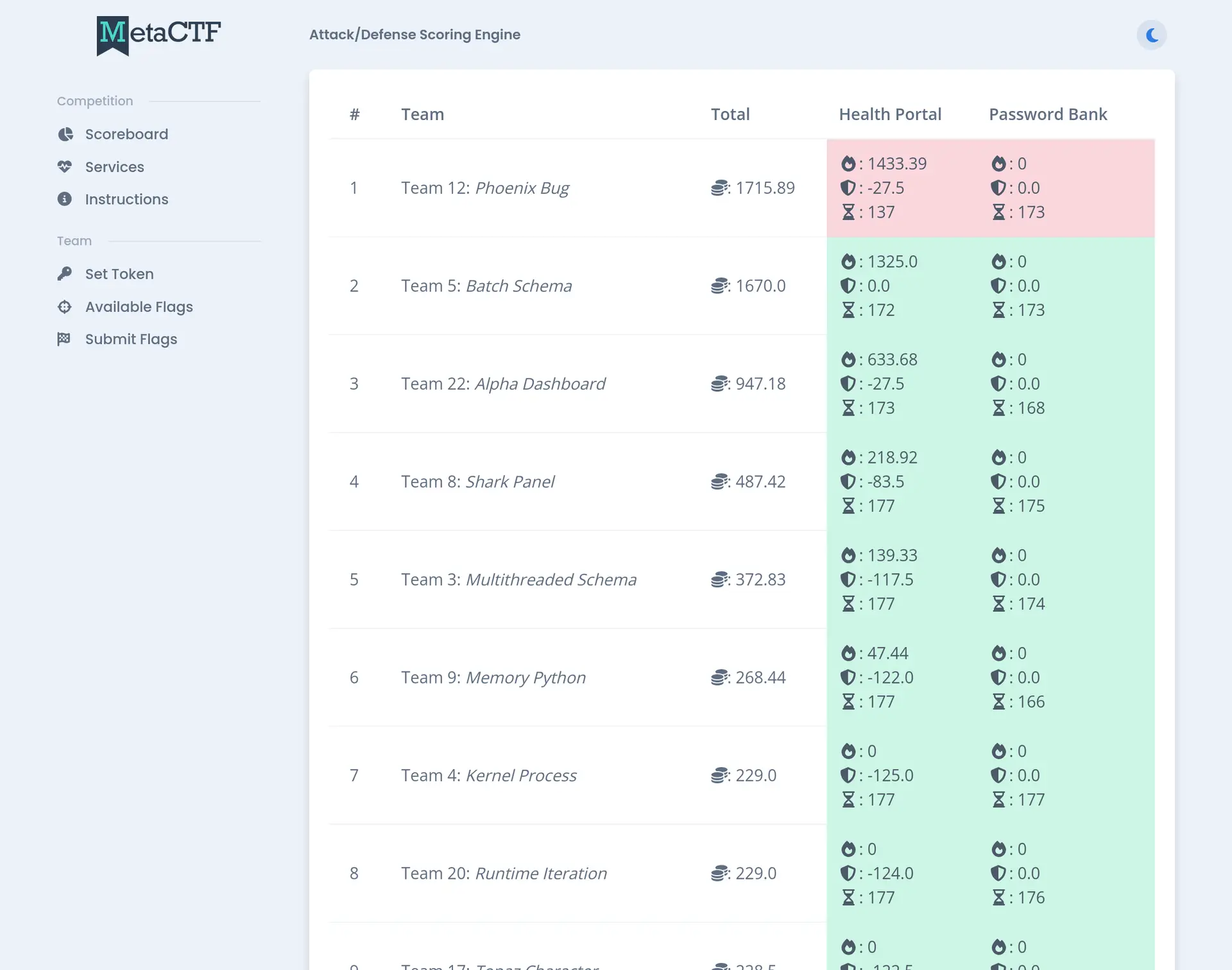
Attack & Defense CTF Competitions
A cybersecurity challenge that offers a traditional and immersive experience on our dedicated platform.
- Challenge your skills as you delve into the intricacies of source code analysis, identifying vulnerabilities, and implementing patches on your own systems.
- Take on the role of both defender and attacker by exploiting identified vulnerabilities on other teams' services to capture flags.
- Our customizable competition platform and scoreboard empower participants to compete effectively, providing a dynamic and engaging environment.
- Participants will receive packet captures of the traffic to and from their services, aiding in the identification of potential exploits.
- Clear instructions and code samples will be provided, ensuring a smooth and educational experience as you navigate the competition.
FREQUENTLY ASKED QUESTIONS
Find out answers to some of the most frequently asked questions about our competition-based training.
- Binary Exploitation
- Cryptography
- Cyber Deception
- Web Exploitation
- Forensics
- Reconnaissance
- Reverse Engineering
- Other