Once we launch the game, we can see that our goal is to battle and retrieve presents, to later trade them for flag parts by talking with the girl.
It seems we can only get one present and trade it for 2 characters of the flag, which is not nearly enough, so we’ll try extracting the game assets and look at what’s exactly going on.
We can use this app to extract assets from Godot games: https://github.com/GDRETools/gdsdecomp
However, when we select the packed file, we get an error that tells us that our package is either encrypted or corrupted.
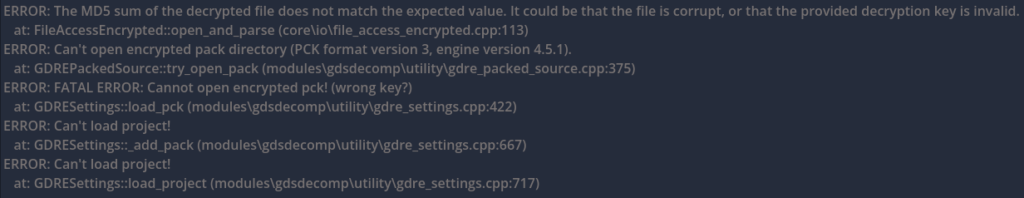
Gdsdecomp supports decrypting encrypted packages, but we need to provide it with an encryption key.
If we search for how to extract encryption keys from Godot games, we come across this project: https://github.com/Titoot/KeyDot
By launching it against the game executable, we manage to extract the key:
.\keydot.exe game.exe
Godot Engine version: 4.6.beta.custom_build
Anchor : Can't open encrypted pack directory.
String VA00000000: 0x1438D6BA0
LEA at00000000000: 0x14293661E
off_* qword VA000: 0x14456C310
Blob VA0000000000: 0x14456C310
32-byte (hex) : EE514AA62489D39E160AD37928F9CF1FD8FA42EA9380EAFC522A0E99D1092D71
We can then set it in the extraction app:
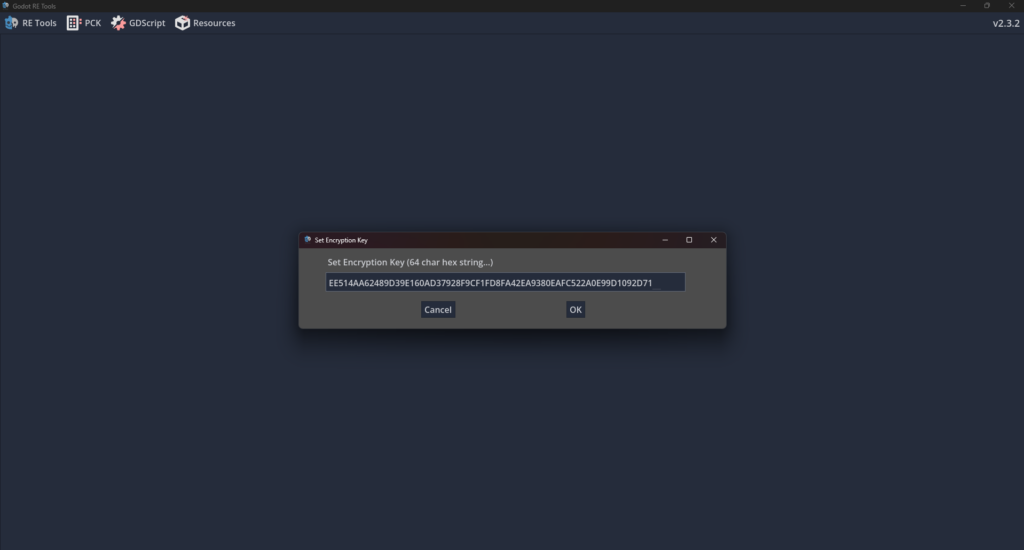
And extract the game package successfully:
We can then open the extracted project in Godot 🙂
We notice that flag characters are stored in the ItemDatabase resource file by tracing them back from the alicia.gd script:
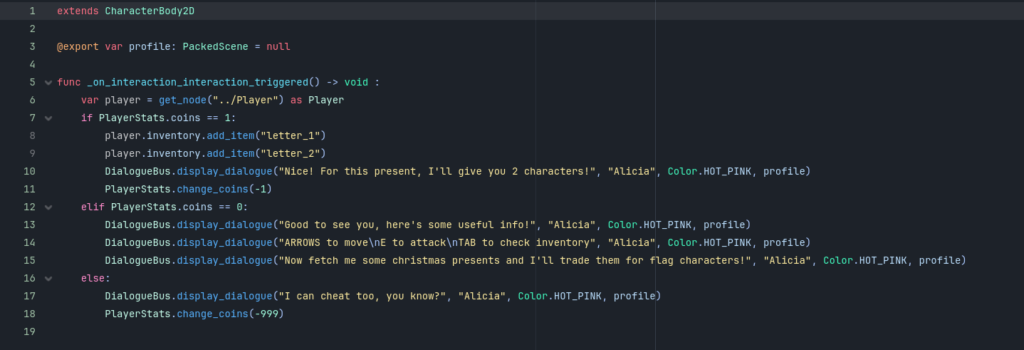
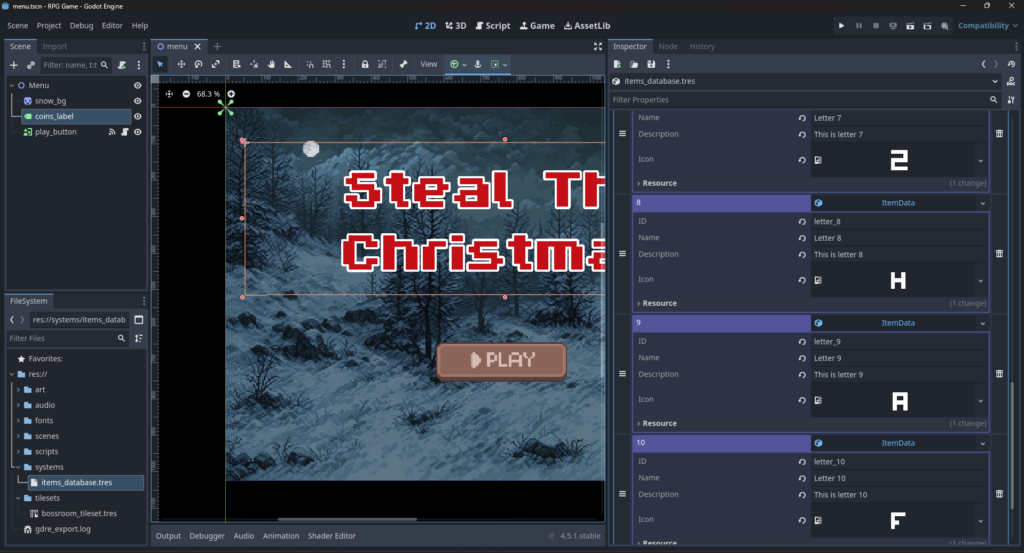
Putting the letters together, we get the following flag:
COOCOZ2HAF
And we can wrap in MetaCTF{} and submit it.