Challenge Summary
In this challenge, you are given a JPEG file that has had its first four bytes replaced with META, causing normal image viewers to fail to open it. You must use a hex editor (or other tool) to put back the original magic bytes and open the repaired image to view the flag.
Background
“Binary” (that is, non-text) files such as images, videos, or executable programs are composed of a series of bytes. The vast majority of file formats start with a short string of bytes formally called the “file signature”, but usually referred to as the “magic bytes”. These are hardcoded, constant values, and serve just to identify the file format that is in use.
For instance, every PNG image starts with (in hexadecimal notation) the values 89 50 4E 47 0D 0A 1A 0A: when interpreted as text, this looks like ‰PNG␍␊␚␊. Every Linux executable starts with 7F 45 4C 46 (␡ELF), every PDF document starts with 25 50 44 46 2D (%PDF-), and so on.
There’s a big list of them all at this link.
The Challenge
We are given a “corrupted image” and a bunch of flavor text about wizards and their aforementioned magic bytes. The description also hints that a hex editor might be of use.
When we download the file, we note that its name is magical_meta.jpg – with that extension, we’d expect its file type to be a JPEG image.
However, trying to open it in an image viewer will fail. Most will just give a generic error. But if you’re lucky, a rare few will give you a more useful error message:
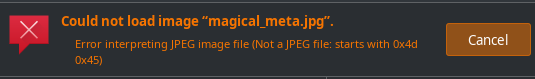
The viewer has refused to open this JPEG file because, well, it’s not a JPEG. The viewer knows that because, as it says, the file starts with hexadecimal bytes 4D 45.
What bytes is a JPEG file supposed to start with? If we peek at that Wikipedia article that was linked earlier and search for JPEG (or JPG), we find a few options:
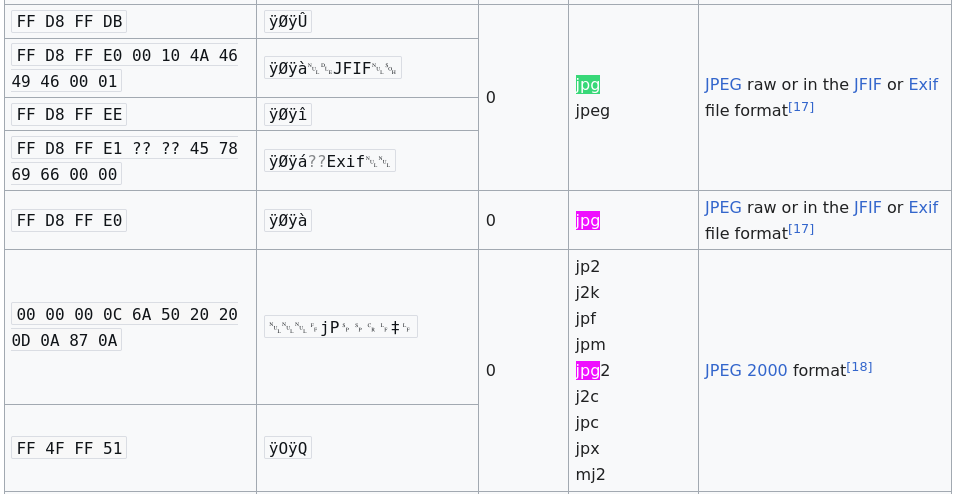
(JPEG 2000 is actually an entirely different, newer file format – this can be somewhat confusing. The top ones are what’s relevant to us.)
And what does our mystery file start with? To figure this out, let’s pop it into a hex editor. The challenge description links one, hexed.it, which works in your web browser: link here. But it’s not a bad idea to have one installed – HxD is a popular choice, and there are also many VSCode hex editor plugins. ImHex is really cool, if perhaps a bit overkill.
In hexed.it, our file looks like this:
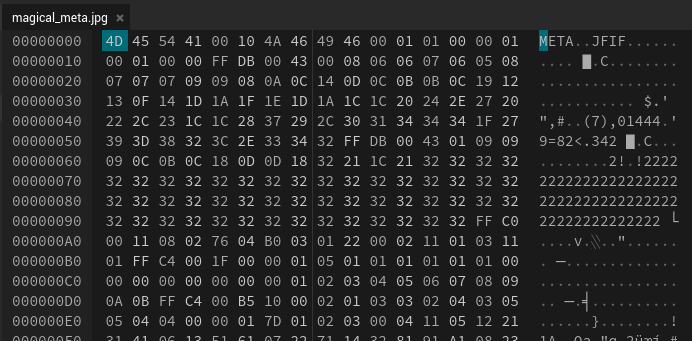
This is a pretty typical hex editor / hex dump layout. The leftmost column shows the index/position within the file (think of it kind of like a line number). The grid in the middle shows the file’s raw bytes, displayed in hexadecimal (every two hex digits is one byte). The right-hand side shows the same bytes, but displayed as ASCII characters – those that are not valid ASCII are rendered as grey dots.
On said right-hand side, note the JFIF part. This matches one of the JPEG file signatures we saw earlier:

In fact, after the first four bytes, it looks like everything matches the magic bytes that we’d expect. So it seems like the “corruption” mentioned in the description was just replacing the first four bytes of the file. Well, we can easily fix that!
Copy the first four bytes, in hex, from the file signature that had JFIF in it: FF D8 FF E0. In hexed.it, put your cursor on the very first byte of the file, and hit Ctrl+V to paste. Specify the following:
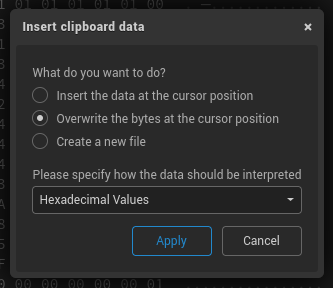
… since we indeed want to overwrite the META bytes, and we want to interpret the values in our clipboard as hexadecimal.
With the file restored to its original state, hit Export, and open the image that downloads:
